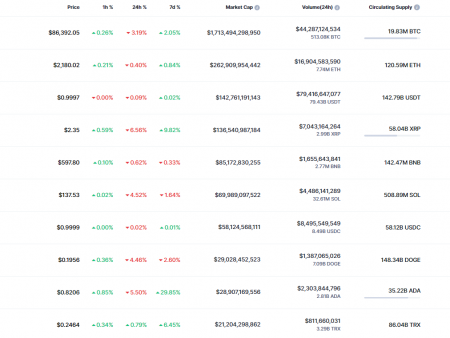
More controversy looms over decentralized finance (DeFi) Solana (SOL) as the crypto community debates maximum extractable value (MEV) tactics.
According to sources, one Solana validator extracted more than $60 million in one month using sandwich attacks. This was done using the Solana blockchain architecture, which facilitates MEV activities such as sandwich attacks to its benefit and to the detriment of users.
On-chain and DeFi analyst, the main developer of DefiLlama, 0xngmi, commented on the matter, highlighting the $60 million profit. “And that’s just profit,” he added. “The overall user loss is higher because you have to enable validator bribes,” users have to pay a fee to prioritize the transaction.
Arsc: Solana validator profiting from MEV sandwich attacks
In fact, the discussion gained momentum after Ben, the core developer of Temporal (@temporal_xyz), posted about the issue on December 10th. Ben uncovered three accounts associated with Arsc, which are actively used to carry out attacks and generate profit.
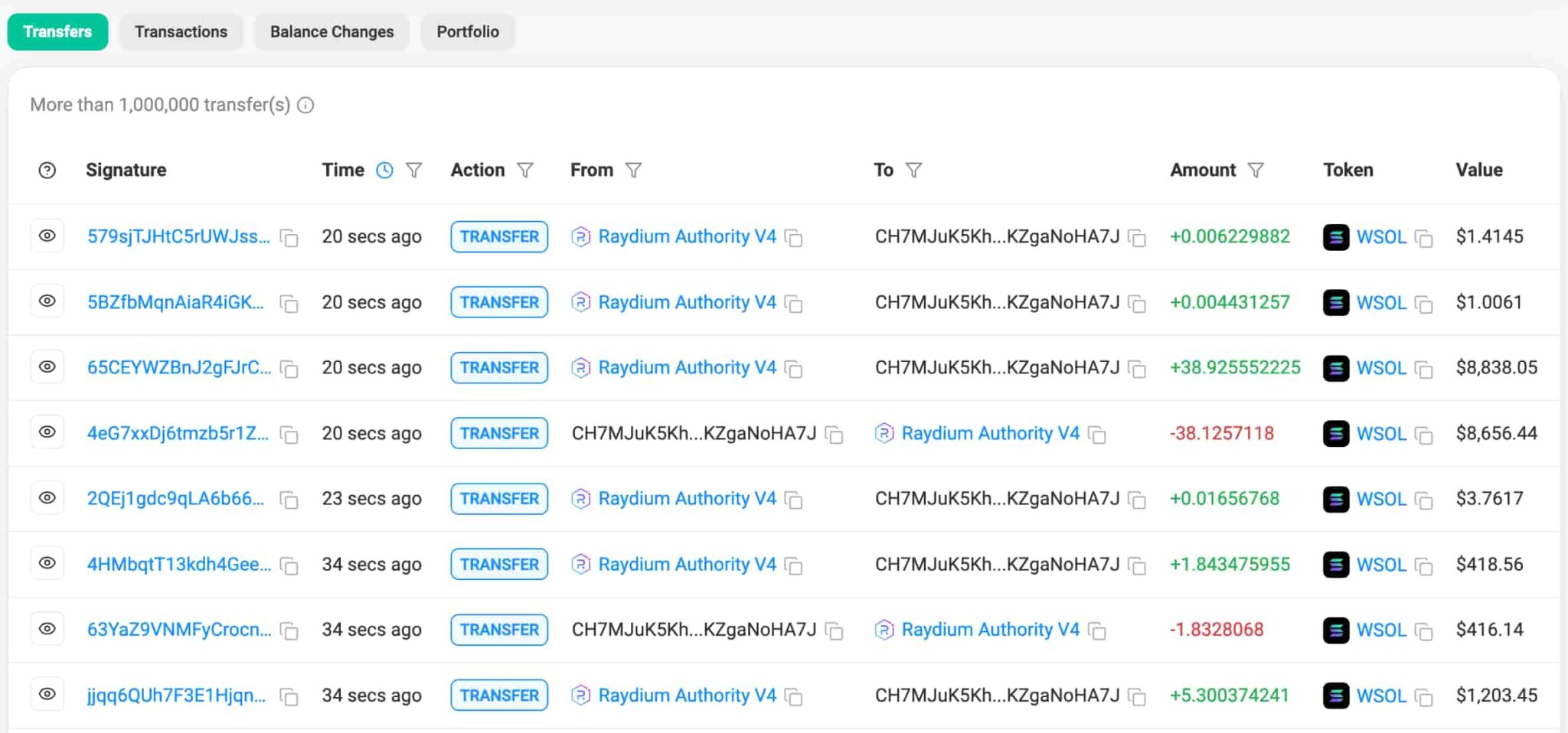
According to the post, Arsc is a Solana validator that uses its block creation privileges to outpace users with a sandwich bot attack, aiming to increase its revenue from maximizing value extraction tactics.
MILLIONS of dollars in MEV are siphoned DAILY by vpe (aka arsc), the leading sandwich bot. But the worst part? It’s not just about MEV, it’s about centralizing MEV. And this is the biggest threat to Solana’s decentralization that I have ever seen.
Solana’s volume is growing rapidly, and… pic.twitter.com/v6mlSQhtg1
— Ben ⌛ (@HypoNyms) December 10, 2024
As a solution to the problem, Ben suggests either whitelisting/blacklisting “good/bad” validators, or using a public mempool. Both solutions, however, involve some kind of central coordination and have drawn criticism from other experts and commentators.
“Whitelist/blacklist simply leads to censorship, centralization and backroom dealings,” said Victor Bunin, protocol specialist at Coinbase. “The way to reduce the number of sandwiches is through better slippage parameterization, intents/solvers, better dex design, or a discounting solution like Flashbots Protect.”
What is the MEV sandwich attack and why Solana?
In the MEV sandwich attack in Solana, attackers exploit the order of transactions to make profits at the expense of ordinary users. This manipulation ensures that the user always gets the worst price and the attacker gets the benefit.
These entities, usually validators or those with access to private mempools, place two transactions around the target user’s transaction: one before purchasing the asset at a low price, and another after selling it at a higher price, thus “squeezing” the user’s transaction.
Essentially, this practice harms users by increasing their transaction costs and reducing the fairness of the trading environment. Few validators benefit as they control the order of transactions in Solana’s leader-based block production system.
Interestingly, Solana’s architecture makes it particularly suitable for such attacks due to its high-speed transaction processing and the absence of an in-protocol mempool. Instead, some validators use private mempools, which allow them to see and manipulate transactions before they are completed. This scenario resulted in significant MEV revenue for these validators, often at the direct cost of user experience and network integrity.
Moreover, Solana’s architecture makes it difficult for outside observers to detect MEV tactics such as sandwich attacks, raising concerns about data ambiguity and questions about how much of Solana’s true economic value (REV) actually comes from predatory value extraction.
This is especially true since SOL proponents often cite REV as the leading metric that puts Solana ahead of competitors such as Ethereum (ETH). However, Mert, CEO of Helius Labs, Solana’s largest RPC vendor, explained that sandwich attacks make up only a small portion of the REV network.
“The latest information about this [sandwich attacks] it’s that the total turnover is expressed in one figure, and that’s what I mean – the vast majority of income comes from prioritization. [transactions] to land faster,” Mert said in the thread.
As events unfold, traders, investors, users and enthusiasts are discussing MEV sandwich attacks and potential solutions. For now, users who don’t want to fall victim to such attacks can use Helius tools or choose chains with built-in MEV protection, such as MultiversX (EGLD).
Featured image from Shutterstock.